- Palo Alto Firewall Download
- Download Palo Alto Firewall Ova File Extension
- Palo Alto Virtual Firewall Download
Download the Panorama OVA files Applicable to the following hypervisors: ESXi KVM Citrix SDX Nutanix Hyper-V OpenStack For an updated list, p How to download the Panorama OVA file - Knowledge Base - Palo Alto Networks. You must have to download Palo Alto virtual Firewall ovf file from your Palo Alto support portal. In this scenario, we will configure the Virtual Palo Alto Firewall in Linux as well as Windows environment. Before starting, it's required you have a minimum of 8GB of RAM with an i5 or i7 processor. To get a Palo Alto virtual firewall working and see how to configure its basic security settings. Downloading the OVA File Go to the page linked below, and log in with the credentials given in class. Downloading the Virtual Machines. Find the 'CNIT 140' section and download the Palo Alto Firewall. Next-Generation Firewall GlobalProtect Threat Prevention Services. I'll be deploying Panorama in ESXi server, where can I download the OVA file? I know this is a very stupid question. I'm following the steps below, but I can't find it under my profile. Palo Alto Networks.
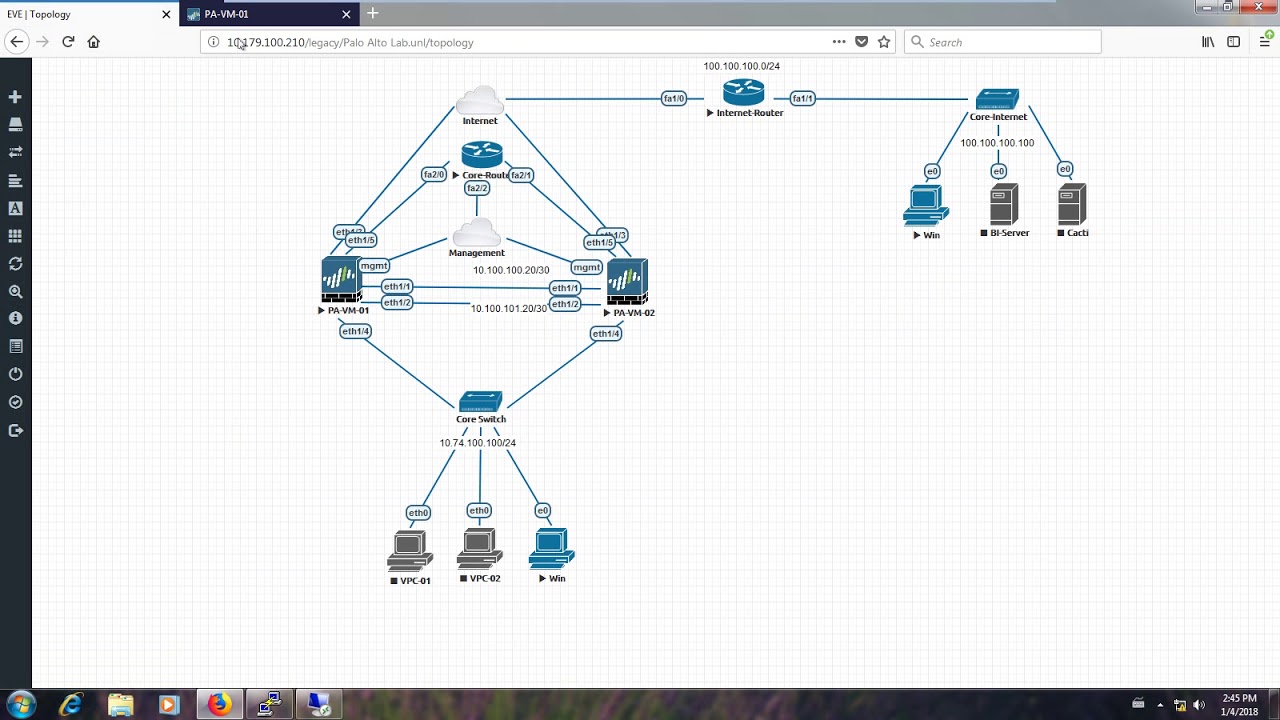
The VM-Series firewall is distributed using the Open Virtualization Alliance (OVA) format, which is a standard method of packaging and deploying virtual machines. You can install this solution on any x86 device that is capable of running VMware ESXi.
In order to deploy a VM-Series firewall, you must be familiar with VMware and vSphere including vSphere networking, ESXi host setup and configuration, and virtual machine guest deployment.
You can deploy one or more instances of the VM-Series firewall on the ESXi server. Where you place the VM-Series firewall on the network depends on your topology. Choose from the following options (for environments that are not using VMware NSX):
- One VM-Series firewall per ESXi host—Every VM server on the ESXi host passes through the firewall before exiting the host for the physical network. VM servers attach to the firewall via virtual standard switches. The guest servers have no other network connectivity and therefore the firewall has visibility and control to all traffic leaving the ESXi host. One variation of this use case is to also require all traffic to flow through the firewall, including server to server (east-west traffic) on the same ESXi host.
- One VM-Series firewall per virtual network—Deploy a VM-Series firewall for every virtual network. If you have designed your network such that one or more ESXi hosts has a group of virtual machines that belong to the internal network, a group that belongs to the external network, and some others to the DMZ, you can deploy a VM-Series firewall to safeguard the servers in each group. If a group or virtual network does not share a virtual switch or port group with any other virtual network, it is completely isolated from all other virtual networks within or across the host(s). Because there is no other physical or virtual path to any other network, the servers on each virtual network must use the firewall to talk to any other network. Therefore, it allows the firewall visibility and control to all traffic leaving the virtual (standard or distributed) switch attached to each virtual network.
- Hybrid environment—Both physical and virtual hosts are used, the VM-Series firewall can be deployed in a traditional aggregation location in place of a physical firewall appliance to achieve the benefits of a common server platform for all devices and to unlink hardware and software upgrade dependencies.
System Requirements
You can create and deploy multiple instances of the VM-Series firewall on an ESXi server. Because each instance of the firewall requires a minimum resource allocation number of CPUs, memory and disk space—on the ESXi server, make sure to conform to the specifications below to ensure optimal performance.
The VM-Series firewall has the following requirements:
The host CPU must be a x86-based Intel or AMD CPU with virtualization extension.
VMware ESXi with vSphere 5.1, 5.5, 6.0, or 6.5 for VM-Series running PAN-OS 8.0. The VM-Series firewall on ESXi is deployed with VMware virtual machine hardware version 9 (vmx-09); no other VMware virtual machine hardware versions are supported.
See VM-Series System Requirements for the minimum hardware requirements for your VM-Series model.
Minimum of two network interfaces (vmNICs). One will be a dedicated vmNIC for the management interface and one for the data interface. You can then add up to eight more vmNICs for data traffic. For additional interfaces, use VLAN Guest Tagging (VGT) on the ESXi server or configure subinterfaces on the firewall.
The use of hypervisor assigned MAC address is enabled by default. vSphere assigns a unique vmNIC MAC address to each dataplane interface of the VM-Series firewall. If you disable the use hypervisor assigned MAC addresses, the VM-Series firewall assigns each interface of a MAC address from its own pool. Because this causes the MAC addresses on each interface to differ, you must enable promiscuous mode (see Before deploying the OVA file, set up virtual standard switch(es) and virtual distributed switch(es) that you will need for the VM-Series firewall.) on the port group of the virtual switch to which the dataplane interfaces of the firewall are attached to allow the firewall to receive frames. If neither promiscuous mode nor hypervisor assigned MAC address is enabled, the firewall will not receive any traffic. This is because vSphere will not forward frames to a virtual machine when the destination MAC address of the frame does not match the vmNIC MAC address.
Data Plane Development Kit (DPDK) is enabled by default on VM-Series firewalls on ESXi. For more information about DPDK, see Enable DPDK on ESXi.
To achieve the best performance out of the VM-Series firewall, you can make the following adjustments to the host before deploying the VM-Series firewall. See Performance Tuning of the VM-Series for ESXi for more information.
Enable DPDK. DPDK allows the host to process packets faster by bypassing the Linux kernel. Instead, interactions with the NIC are performed using drivers and the DPDK libraries.
Enable SR-IOV. Single root I/O virtualization (SR-IOV) allows a single PCIe physical device under a single root port to appear to be multiple separate physical devices to the hypervisor or guest.
Do not configure a vSwitch on the physical port on which you enable SR-IOV. To communicate with the host or other virtual machines on the network, the VM-Series firewall must have exclusive access to the physical port and associated virtual functions (VFs) on that interface.
Enable multi-queue support for NICs. Multi-queue allows network performance to scale with the number of vCPUs and allows for parallel packet processing by creating multiple TX and RX queues.
Note:-
Do not use the VMware snapshots functionality on the VM-Series on ESXi. Snapshots can impact performance and result in intermittent and inconsistent packet loss.See VMWare's best practice recommendation with using snapshots.
If you need configuration backups, use Panorama or Export named configuration snapshot from the firewall (Device > Set up > Operations). Using the Export named configuration snapshot exports the active configuration (running-config.xml) on the firewall and allows you to save it to any network location.
Limitations
The VM-Series firewall functionality is very similar to the Palo Alto Networks hardware firewalls, but with the following limitations:
Dedicated CPU cores are recommended.
High Availability (HA) Link Monitoring is not supported on VM-Series firewalls on ESXi. Use Path Monitoring to verify connectivity to a target IP address or to the next hop IP address.
Up to 10 total ports can be configured; this is a VMware limitation. One port will be used for management traffic and up to 9 can be used for data traffic.
Only the vmxnet3 driver is supported.
Virtual systems are not supported.
vMotion of the VM-Series firewall is not supported. However, the VM-Series firewall can secure guest virtual machines that have migrated to a new destination host, if the source and destination hosts are members of all vSphere Distributed Switches that the guest virtual machine used for networking.
VLAN trunking must be enabled on the ESXi vSwitch port-groups that are connected to the interfaces (if configured in vwire mode) on the VM-Series firewall.
To use PCI devices with the VM-Series firewall on ESXi, memory mapped I/O (MMIO) must be below 4GB. You can disable MMIO above 4GB in your server's BIOS. This is an ESXi limitation.
Deploy Paloalto VM-Series
Register your VM-Series firewall and obtain the OVA file from the Palo Alto Networks Customer Support web site.
Note:- The OVA is downloaded as a zip archive that is expanded into three files: the .ovf extension is for the OVF descriptor file that contains all metadata about the package and its contents; the .mf extension is for the OVF manifest file that contains the SHA-1 digests of individual files in the package; and the .vmdk extension is for the virtual disk image file that contains the virtualized version of the firewall.
Before deploying the OVA file, set up virtual standard switch(es) and virtual distributed switch(es) that you will need for the VM-Series firewall.
If you are deploying the VM-Series firewall with Layer 3 interfaces, your firewall will use Hypervisor Assigned MAC Addresses by default. If you choose to disable the use of hypervisor assigned MAC address, you must configure (set to Accept) any virtual switch attached to the VM-Series firewall to allow the following modes:
- Promiscuous mode
- MAC address changes
- Forged transmits
Log in to vCenter from the vSphere Web Client. You can also go directly to the target ESXi host if needed.
From the vSphere client, select FileDeploy OVF Template.
Browse to the OVA file that you downloaded and select the file and then click Next. Review the templates details window and then click Next again.
Name the VM-Series firewall instance and in the Inventory Location window, select a Data Center and Folder and click Next
Select an ESXi host for the VM-Series firewall and click Next.
Select the datastore to use for the VM-Series firewall and click Next ( Default virtual disk format is thick and you may change to Thin )
Select the networks to use
Review the details window, select the Power on after deployment check box and then click Next.
Initial Configuration

Access the console of the VM-Series firewall.
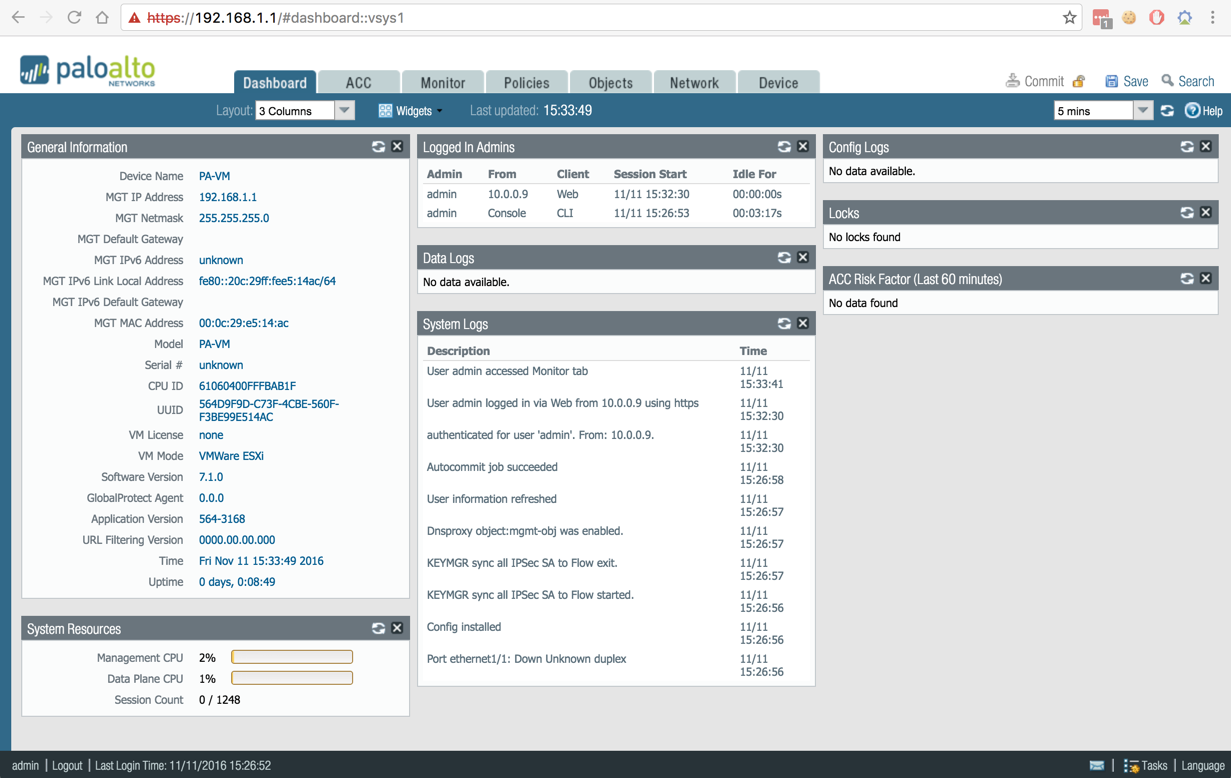
Enter the default username/password (admin/admin) to log in.
Enter configure to switch to configuration mode.
Configure the network access settings for the management interface. You should restrict access to the firewall and isolate the management network. Additionally, do not make the allowed network larger than necessary and never configure the allowed source as 0.0.0.0/0.
Now you have to exit from configuration mode by entering exit
Access the Firewall from a web browser
Open the Browse and type the IP you have assigned to the VM to access the console.
Enter the credentials
You are logged in to the PA firewall and you can start using it
Conclusion
Here we shared detailed information about the deployment of paloalto VM-Series edition and steps to follow for a successful deployment. Also what is the limitation and system requirements for a virtual edition with reference links have been added to it, you have to refer them before starting the deployment
Palo Alto Networks VM-Series Virtualised Firewall
The Palo Alto Networks VM-Series features three virtualised next-generation firewall models – the VM-100, VM-200, and VM-300. These platforms are supported on the VMware ESXi 4.1 and ESXi 5.0 platforms. 2, 4, or 8 CPU cores on your virtualised server platforms can be assigned for next-generation firewall processing.
With 4 CPU cores running, the VM-Series delivers up to 1 Gbps firewall throughput with App-ID enabled. To ensure that management is accessible to you during heavy traffic, the data and control plane are separated. In addition, our unique single-pass software architecture processes functions in a single pass to reduce latency.
The VM-Series runs PAN-OSTM, a security-specific operating system that:
- Safely enables intra-virtual machine traffic
- Protects you against all known and unknown threats
- Integrates flexibly in the virtualised environment at layers 1, 2, or 3
Our PAN-OS next-generation firewall capabilities allow you to tie your security policies to virtual machine adds, moves and changes, and to create security policies that instantly sync with virtual workload creation.
VM-300 Overview
- 250,000 max sessions
- 2,000 IPSec VPN tunnels/tunnel interfaces
- 500 SSL VPN Users
- 40 security zones
- 5,000 max number of policies
- 10,000 address objects
- 1Gbps Firewall Throughput (App-ID enabled)*
- 600 Mbps Threat Prevention Throughput*
- 250 Mbps IPSec VPN Throughput*
- 8,000 New sessions per second*
VM-200 Overview
- 100,000 max sessions
- 500 IPSec VPN tunnels/tunnel interfaces
- 200 SSL VPN Users
- 20 security zones
- 2,000 max number of policies
- 4,000 address objects
- 1Gbps Firewall Throughput (App-ID enabled)*
- 600 Mbps Threat Prevention Throughput*
- 250 Mbps IPSec VPN Throughput*
- 8,000 New sessions per second*
VM-100 Overview
- 50,000 max sessions
- 25 IPSec VPN tunnels/tunnel interfaces
- 25 SSL VPN Users
- 10 security zones
- 250 max number of policies
- 2,500 address objects
- 1Gbps Firewall Throughput (App-ID enabled)*
- 600 Mbps Threat Prevention Throughput*
- 250 Mbps IPSec VPN Throughput*
- 8,000 New sessions per second*
*Performance and capacities are measured under ideal testing conditions using PAN-OS 5.0 and 4 CPU cores.
Resources
Palo Alto Networks VM-Series Datasheet
The Palo Alto Networks™ VM-Series extends secure application enablement into virtualised environments while addressing key virtualisation security challenges: tracking security policies to virtual machine movement with dynamic address objects and integration with orchestration systems using a powerful XML management API.- 3-Page PDF: VM-Series Datasheet
Palo Alto Networks Firewall Overview
Palo Alto Networks Next Generation Firewall Overview- 8-Page PDF: Palo Alto Networks Firewall Oveview
Palo Alto Networks Panorama
Panorama provides centralised policy and device management over a network of Palo Alto Networks™ next-generation firewalls.- 5-Page PDF: Panorama Specsheet
Security Subscription Options
Wildfire
WildFire automatically protects your networks from new and customised malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends the threat prevention capabilities of the next-generation firewall to tackle some of the most challenging threats in the world today, and does so with full visibility and enforcement at up to 10Gbps.- 6-Page PDF: WildFire Datasheet
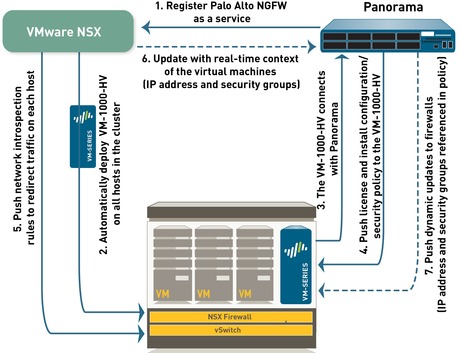
GlobalProtect
GlobalProtect bridges the divide between remote users and the enterprise security policy. First and foremost, GlobalProtect not only provides VPN access to corporate network but also extends enterprise security policy to all users regardless of their location. GlobalProtect frees enterprises from having to deploy different stacks of non-deterministic and inconsistent security solutions like proxy and VPN for their remote users. GlobalProtect connects users to the next-generation firewall to deliver full visibility, control and threat prevention to all enterprise traffic.
- 3-Page PDF: GlobalProtect Datasheet

URL Filtering
Fully integrated URL filtering database enables granular control over web browsing activity, complementing safe application enablement policies.- 2-Page PDF:URL Filtering Datasheet
Threat Prevention
Fully integrated real-time threat prevention protects enterprise networks from a wide range of threats, complementing the policy-based application visibility and control that the Palo Alto Networks next-generation firewalls deliver.- 4-Page PDF: Integrated Threat Prevention Datasheet
Palo Alto Firewall Download
Support Services Options
Standard Support
Standard customer support and maintenance provides customers with baseline services for maintaining the next-generation firewall. This option includes the following features:- New Releases, Product Updates, and Patches: Provides the latest product innovations and bug fixes.
- Updated Threat Databases: App-ID, URL, vulnerability, and GlobalProtect gateway updates are available for automatic or manual download to your firewalls
- Online Customer Support Portal: A feature rich platform providing access to product documentation, problem resolution databases, peer-to-peer social interaction, and customer support case management
- Business Hour Assisted Support: Get access to support engineers for help during normal business hours
- Hardware Return then Replace Coverage: In the event of hardware failure, return the failed equipment and receive a replacement
- 2-Page PDF: Support Services Overview
Premium Support
Organisations choose premium customer support and maintenance for faster assistance and increased support engineer availability for the most critical issues. This option includes the following features:- All Elements of Standard Customer Support and Maintenance are included with this option
- 24×7 Access to Technical Assistance Centers: Support engineers are available to assist with issues around the clock.
- Priority Response to Support Inquiries:Whether submitted by phone or online, premium support customers receive priority access to available customer support engineers.
- Next Business Day Ship Parts and Hardware Replacement: Provides fast turnaround for hardware replacement. For an additional fee, RMA and Hardware Replacement services can be upgraded to 4 Hour Ship, or On Site Spares for immediate replacement of failed hardware.
- Technical Account Management (Optional):Subscription-based extension of the Premium Support program that provides dedicated customer advocacy for enterprises with unique or complex support requirements. The technical account manager will be familiar with the customer's specific implementation, acting as a bi-directional communications conduit between Palo Alto Networks and the customer.
Download Palo Alto Firewall Ova File Extension
- 2-Page PDF: Support Services Overview
Palo Alto Virtual Firewall Download
The VM-Series firewall is distributed using the Open Virtualization Alliance (OVA) format, which is a standard method of packaging and deploying virtual machines. You can install this solution on any x86 device that is capable of running VMware ESXi.
In order to deploy a VM-Series firewall, you must be familiar with VMware and vSphere including vSphere networking, ESXi host setup and configuration, and virtual machine guest deployment.
You can deploy one or more instances of the VM-Series firewall on the ESXi server. Where you place the VM-Series firewall on the network depends on your topology. Choose from the following options (for environments that are not using VMware NSX):
- One VM-Series firewall per ESXi host—Every VM server on the ESXi host passes through the firewall before exiting the host for the physical network. VM servers attach to the firewall via virtual standard switches. The guest servers have no other network connectivity and therefore the firewall has visibility and control to all traffic leaving the ESXi host. One variation of this use case is to also require all traffic to flow through the firewall, including server to server (east-west traffic) on the same ESXi host.
- One VM-Series firewall per virtual network—Deploy a VM-Series firewall for every virtual network. If you have designed your network such that one or more ESXi hosts has a group of virtual machines that belong to the internal network, a group that belongs to the external network, and some others to the DMZ, you can deploy a VM-Series firewall to safeguard the servers in each group. If a group or virtual network does not share a virtual switch or port group with any other virtual network, it is completely isolated from all other virtual networks within or across the host(s). Because there is no other physical or virtual path to any other network, the servers on each virtual network must use the firewall to talk to any other network. Therefore, it allows the firewall visibility and control to all traffic leaving the virtual (standard or distributed) switch attached to each virtual network.
- Hybrid environment—Both physical and virtual hosts are used, the VM-Series firewall can be deployed in a traditional aggregation location in place of a physical firewall appliance to achieve the benefits of a common server platform for all devices and to unlink hardware and software upgrade dependencies.
System Requirements
You can create and deploy multiple instances of the VM-Series firewall on an ESXi server. Because each instance of the firewall requires a minimum resource allocation number of CPUs, memory and disk space—on the ESXi server, make sure to conform to the specifications below to ensure optimal performance.
The VM-Series firewall has the following requirements:
The host CPU must be a x86-based Intel or AMD CPU with virtualization extension.
VMware ESXi with vSphere 5.1, 5.5, 6.0, or 6.5 for VM-Series running PAN-OS 8.0. The VM-Series firewall on ESXi is deployed with VMware virtual machine hardware version 9 (vmx-09); no other VMware virtual machine hardware versions are supported.
See VM-Series System Requirements for the minimum hardware requirements for your VM-Series model.
Minimum of two network interfaces (vmNICs). One will be a dedicated vmNIC for the management interface and one for the data interface. You can then add up to eight more vmNICs for data traffic. For additional interfaces, use VLAN Guest Tagging (VGT) on the ESXi server or configure subinterfaces on the firewall.
The use of hypervisor assigned MAC address is enabled by default. vSphere assigns a unique vmNIC MAC address to each dataplane interface of the VM-Series firewall. If you disable the use hypervisor assigned MAC addresses, the VM-Series firewall assigns each interface of a MAC address from its own pool. Because this causes the MAC addresses on each interface to differ, you must enable promiscuous mode (see Before deploying the OVA file, set up virtual standard switch(es) and virtual distributed switch(es) that you will need for the VM-Series firewall.) on the port group of the virtual switch to which the dataplane interfaces of the firewall are attached to allow the firewall to receive frames. If neither promiscuous mode nor hypervisor assigned MAC address is enabled, the firewall will not receive any traffic. This is because vSphere will not forward frames to a virtual machine when the destination MAC address of the frame does not match the vmNIC MAC address.
Data Plane Development Kit (DPDK) is enabled by default on VM-Series firewalls on ESXi. For more information about DPDK, see Enable DPDK on ESXi.
To achieve the best performance out of the VM-Series firewall, you can make the following adjustments to the host before deploying the VM-Series firewall. See Performance Tuning of the VM-Series for ESXi for more information.
Enable DPDK. DPDK allows the host to process packets faster by bypassing the Linux kernel. Instead, interactions with the NIC are performed using drivers and the DPDK libraries.
Enable SR-IOV. Single root I/O virtualization (SR-IOV) allows a single PCIe physical device under a single root port to appear to be multiple separate physical devices to the hypervisor or guest.
Do not configure a vSwitch on the physical port on which you enable SR-IOV. To communicate with the host or other virtual machines on the network, the VM-Series firewall must have exclusive access to the physical port and associated virtual functions (VFs) on that interface.
Enable multi-queue support for NICs. Multi-queue allows network performance to scale with the number of vCPUs and allows for parallel packet processing by creating multiple TX and RX queues.
Note:-
Do not use the VMware snapshots functionality on the VM-Series on ESXi. Snapshots can impact performance and result in intermittent and inconsistent packet loss.See VMWare's best practice recommendation with using snapshots.
If you need configuration backups, use Panorama or Export named configuration snapshot from the firewall (Device > Set up > Operations). Using the Export named configuration snapshot exports the active configuration (running-config.xml) on the firewall and allows you to save it to any network location.
Limitations
The VM-Series firewall functionality is very similar to the Palo Alto Networks hardware firewalls, but with the following limitations:
Dedicated CPU cores are recommended.
High Availability (HA) Link Monitoring is not supported on VM-Series firewalls on ESXi. Use Path Monitoring to verify connectivity to a target IP address or to the next hop IP address.
Up to 10 total ports can be configured; this is a VMware limitation. One port will be used for management traffic and up to 9 can be used for data traffic.
Only the vmxnet3 driver is supported.
Virtual systems are not supported.
vMotion of the VM-Series firewall is not supported. However, the VM-Series firewall can secure guest virtual machines that have migrated to a new destination host, if the source and destination hosts are members of all vSphere Distributed Switches that the guest virtual machine used for networking.
VLAN trunking must be enabled on the ESXi vSwitch port-groups that are connected to the interfaces (if configured in vwire mode) on the VM-Series firewall.
To use PCI devices with the VM-Series firewall on ESXi, memory mapped I/O (MMIO) must be below 4GB. You can disable MMIO above 4GB in your server's BIOS. This is an ESXi limitation.
Deploy Paloalto VM-Series
Register your VM-Series firewall and obtain the OVA file from the Palo Alto Networks Customer Support web site.
Note:- The OVA is downloaded as a zip archive that is expanded into three files: the .ovf extension is for the OVF descriptor file that contains all metadata about the package and its contents; the .mf extension is for the OVF manifest file that contains the SHA-1 digests of individual files in the package; and the .vmdk extension is for the virtual disk image file that contains the virtualized version of the firewall.
Before deploying the OVA file, set up virtual standard switch(es) and virtual distributed switch(es) that you will need for the VM-Series firewall.
If you are deploying the VM-Series firewall with Layer 3 interfaces, your firewall will use Hypervisor Assigned MAC Addresses by default. If you choose to disable the use of hypervisor assigned MAC address, you must configure (set to Accept) any virtual switch attached to the VM-Series firewall to allow the following modes:
- Promiscuous mode
- MAC address changes
- Forged transmits
Log in to vCenter from the vSphere Web Client. You can also go directly to the target ESXi host if needed.
From the vSphere client, select FileDeploy OVF Template.
Browse to the OVA file that you downloaded and select the file and then click Next. Review the templates details window and then click Next again.
Name the VM-Series firewall instance and in the Inventory Location window, select a Data Center and Folder and click Next
Select an ESXi host for the VM-Series firewall and click Next.
Select the datastore to use for the VM-Series firewall and click Next ( Default virtual disk format is thick and you may change to Thin )
Select the networks to use
Review the details window, select the Power on after deployment check box and then click Next.
Initial Configuration
Access the console of the VM-Series firewall.
Enter the default username/password (admin/admin) to log in.
Enter configure to switch to configuration mode.
Configure the network access settings for the management interface. You should restrict access to the firewall and isolate the management network. Additionally, do not make the allowed network larger than necessary and never configure the allowed source as 0.0.0.0/0.
Now you have to exit from configuration mode by entering exit
Access the Firewall from a web browser
Open the Browse and type the IP you have assigned to the VM to access the console.
Enter the credentials
You are logged in to the PA firewall and you can start using it
Conclusion
Here we shared detailed information about the deployment of paloalto VM-Series edition and steps to follow for a successful deployment. Also what is the limitation and system requirements for a virtual edition with reference links have been added to it, you have to refer them before starting the deployment
Palo Alto Networks VM-Series Virtualised Firewall
The Palo Alto Networks VM-Series features three virtualised next-generation firewall models – the VM-100, VM-200, and VM-300. These platforms are supported on the VMware ESXi 4.1 and ESXi 5.0 platforms. 2, 4, or 8 CPU cores on your virtualised server platforms can be assigned for next-generation firewall processing.
With 4 CPU cores running, the VM-Series delivers up to 1 Gbps firewall throughput with App-ID enabled. To ensure that management is accessible to you during heavy traffic, the data and control plane are separated. In addition, our unique single-pass software architecture processes functions in a single pass to reduce latency.
The VM-Series runs PAN-OSTM, a security-specific operating system that:
- Safely enables intra-virtual machine traffic
- Protects you against all known and unknown threats
- Integrates flexibly in the virtualised environment at layers 1, 2, or 3
Our PAN-OS next-generation firewall capabilities allow you to tie your security policies to virtual machine adds, moves and changes, and to create security policies that instantly sync with virtual workload creation.
VM-300 Overview
- 250,000 max sessions
- 2,000 IPSec VPN tunnels/tunnel interfaces
- 500 SSL VPN Users
- 40 security zones
- 5,000 max number of policies
- 10,000 address objects
- 1Gbps Firewall Throughput (App-ID enabled)*
- 600 Mbps Threat Prevention Throughput*
- 250 Mbps IPSec VPN Throughput*
- 8,000 New sessions per second*
VM-200 Overview
- 100,000 max sessions
- 500 IPSec VPN tunnels/tunnel interfaces
- 200 SSL VPN Users
- 20 security zones
- 2,000 max number of policies
- 4,000 address objects
- 1Gbps Firewall Throughput (App-ID enabled)*
- 600 Mbps Threat Prevention Throughput*
- 250 Mbps IPSec VPN Throughput*
- 8,000 New sessions per second*
VM-100 Overview
- 50,000 max sessions
- 25 IPSec VPN tunnels/tunnel interfaces
- 25 SSL VPN Users
- 10 security zones
- 250 max number of policies
- 2,500 address objects
- 1Gbps Firewall Throughput (App-ID enabled)*
- 600 Mbps Threat Prevention Throughput*
- 250 Mbps IPSec VPN Throughput*
- 8,000 New sessions per second*
*Performance and capacities are measured under ideal testing conditions using PAN-OS 5.0 and 4 CPU cores.
Resources
Palo Alto Networks VM-Series Datasheet
The Palo Alto Networks™ VM-Series extends secure application enablement into virtualised environments while addressing key virtualisation security challenges: tracking security policies to virtual machine movement with dynamic address objects and integration with orchestration systems using a powerful XML management API.- 3-Page PDF: VM-Series Datasheet
Palo Alto Networks Firewall Overview
Palo Alto Networks Next Generation Firewall Overview- 8-Page PDF: Palo Alto Networks Firewall Oveview
Palo Alto Networks Panorama
Panorama provides centralised policy and device management over a network of Palo Alto Networks™ next-generation firewalls.- 5-Page PDF: Panorama Specsheet
Security Subscription Options
Wildfire
WildFire automatically protects your networks from new and customised malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends the threat prevention capabilities of the next-generation firewall to tackle some of the most challenging threats in the world today, and does so with full visibility and enforcement at up to 10Gbps.- 6-Page PDF: WildFire Datasheet
GlobalProtect
GlobalProtect bridges the divide between remote users and the enterprise security policy. First and foremost, GlobalProtect not only provides VPN access to corporate network but also extends enterprise security policy to all users regardless of their location. GlobalProtect frees enterprises from having to deploy different stacks of non-deterministic and inconsistent security solutions like proxy and VPN for their remote users. GlobalProtect connects users to the next-generation firewall to deliver full visibility, control and threat prevention to all enterprise traffic.
- 3-Page PDF: GlobalProtect Datasheet
URL Filtering
Fully integrated URL filtering database enables granular control over web browsing activity, complementing safe application enablement policies.- 2-Page PDF:URL Filtering Datasheet
Threat Prevention
Fully integrated real-time threat prevention protects enterprise networks from a wide range of threats, complementing the policy-based application visibility and control that the Palo Alto Networks next-generation firewalls deliver.- 4-Page PDF: Integrated Threat Prevention Datasheet
Palo Alto Firewall Download
Support Services Options
Standard Support
Standard customer support and maintenance provides customers with baseline services for maintaining the next-generation firewall. This option includes the following features:- New Releases, Product Updates, and Patches: Provides the latest product innovations and bug fixes.
- Updated Threat Databases: App-ID, URL, vulnerability, and GlobalProtect gateway updates are available for automatic or manual download to your firewalls
- Online Customer Support Portal: A feature rich platform providing access to product documentation, problem resolution databases, peer-to-peer social interaction, and customer support case management
- Business Hour Assisted Support: Get access to support engineers for help during normal business hours
- Hardware Return then Replace Coverage: In the event of hardware failure, return the failed equipment and receive a replacement
- 2-Page PDF: Support Services Overview
Premium Support
Organisations choose premium customer support and maintenance for faster assistance and increased support engineer availability for the most critical issues. This option includes the following features:- All Elements of Standard Customer Support and Maintenance are included with this option
- 24×7 Access to Technical Assistance Centers: Support engineers are available to assist with issues around the clock.
- Priority Response to Support Inquiries:Whether submitted by phone or online, premium support customers receive priority access to available customer support engineers.
- Next Business Day Ship Parts and Hardware Replacement: Provides fast turnaround for hardware replacement. For an additional fee, RMA and Hardware Replacement services can be upgraded to 4 Hour Ship, or On Site Spares for immediate replacement of failed hardware.
- Technical Account Management (Optional):Subscription-based extension of the Premium Support program that provides dedicated customer advocacy for enterprises with unique or complex support requirements. The technical account manager will be familiar with the customer's specific implementation, acting as a bi-directional communications conduit between Palo Alto Networks and the customer.
Download Palo Alto Firewall Ova File Extension
- 2-Page PDF: Support Services Overview
